The User Experience of Security
Recently we saw the launch of the newest iPhone and accompanying mobile operating system. One of the new noteworthy features is the incorporation of a fingerprint scanner into the home button or screen of the new iPhones.ÂÂ
This scanner removes the need for a password or PIN in order to unlock the phone or authenticate purchases. Using the app store, or in-app purchases the user can complete the transaction using their fingerprint where previously they were required to enter the password associated with their Apple ID.
There is a lot of interest surrounding the iPhone fingerprint scanner, but Apple is not the first smartphone manufacturer to use biometric data.  Android phones such as the Samsung Galaxy use the front camera and facial recognition in order to unlock the phone, and there have been other attempts on other systems to solve what I call the password conundrum.ÂÂ
These new (and cool) features are an acknowledgement that we have reached a breaking point when it comes to the number and complexity of usernames, passwords and PINs that we are required to remember on a daily basis. Because of the incredible cognitive load that current password systems require, we end up breaking the very rules that were put in place to protect us.ÂÂ
We write down our passwords, we use the same password over and over again, we use the bare minimum level of complexity the systems will allow… and sometimes that isn’t even enough.ÂÂ
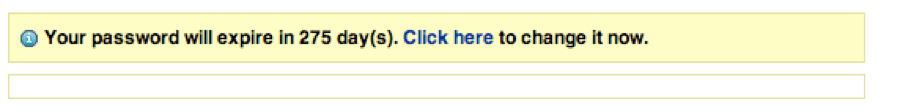
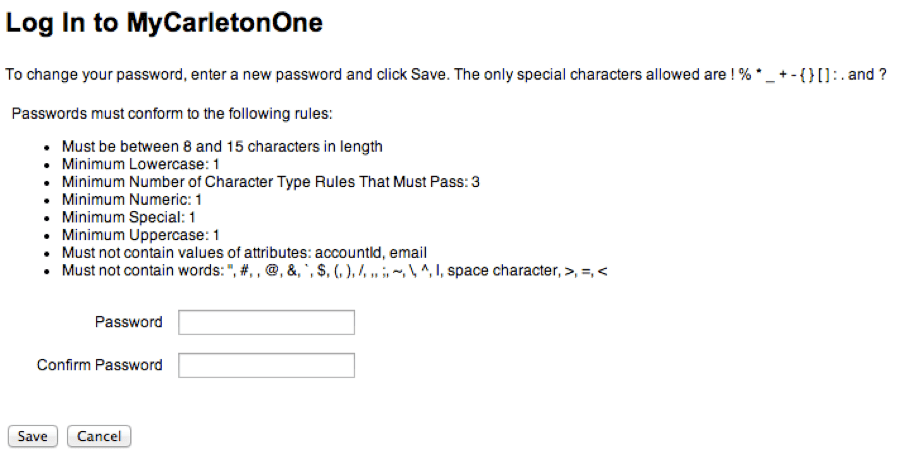
How many times have you had to reset the password for your multiple email accounts, Groupon, banking, your laptop, your phone, your tablet, your timesheet software… you get the picture. And when you do, you have to wrestle with things like this:
And this:
Does the answer to this dilemma lie in the use biometric passwords? Fingerprints, voiceprints, iris and facial scans? We only have a finite number of fingers to print. What happens when those systems get hacked? What happens when through the use of our fingerprints, hackers are able to tie our mobile phones, bank accounts, credit cards and God forbid, our iTunes accounts together?
In May, I had the pleasure of attending DefCon in Las Vegas. DefCon is an international computer security convention held annually in Las Vegas, and one of the biggest of its kind. Between the parties in the penthouse suites and… well more parties, I got to broach the subject of security and UX with some of the security experts who gathered there.ÂÂ
Everyone I spoke to seemed to agree that we have reached the limit of what human beings can reasonably be expected to contend with. As technology moves forward and we’re able to access more and more services online, the number of passwords we must remember continues to increase. As we place more and more of our personal lives online, the complexity of those passwords also continues to increase.ÂÂ
One of the issues with biometric security is that when your faceprint, or your fingerprint gets hacked… you can’t exactly change it, like you would the password to your email account.ÂÂ
The answer according to some of the experts I chatted with lies in multi-factor security.  i.e. you scan your fingerprint, which generates a random code, and that code is what you type in to unlock the system. This dual layer of security makes it harder to hack, and you have the advantage of not having to remember passwords.ÂÂ
For those of us without fancy phones or iris scanners we can see mulit layer security at play in applications such as Datavault, LastPass, or Kaspersky.
These types of applications allow you to store your passwords securely and allow you to log on to site and services either through the software or a browser plugin. The downside of course is that they use up additional resources, slightly slowing down your browsing experience.ÂÂ
In a world that is increasingly concerned with privacy and security, we are in fact a long way away from solving the password problem in any kind of way that would satisfy a usability expert.ÂÂ
Comments
Related Articles